- Splunk Answers
- :
- Splunk Administration
- :
- Installation
- :
- Open multiple receiving ports on a indexer cluster
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I would like to separate my data streams by opening three receving ports.
I have a multisite indexer cluster and I have created an app with this default inputs.conf file
[tcp://9998]
disabled = 0
index = iscore_test
sourcetype = iscore_test
connection_host = ip
[tcp://9999]
disabled = 0
index = iscore_prod
sourcetype = iscore_prod
connection_host = ip
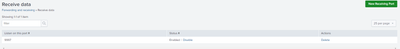
But when I check the receiving ports on the indexer it only shows the 9997 (that I would like to use just for splunk internal logs)
I think there is a faster way to do this rather than set the receiving ports manually in each indexer. I already checked and the app that I created was successfully copied to the indexers.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @aguilard,
if you're speaking of forwarding and receiving between Splunk systems (as it seeems from your screenshot), the inputs.conf that you used are wrong, these are for TCP network inputs.
as you can read at https://docs.splunk.com/Documentation/Splunk/9.1.2/Admin/Inputsconf#inputs.conf.example , , the correct ones for forwarding and receiving are
[splunktcp://:9997]
disabled = 0
[splunktcp://:9998]
disabled = 0
[splunktcp://:9999]
disabled = 0Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @aguilard,
if you're speaking of forwarding and receiving between Splunk systems (as it seeems from your screenshot), the inputs.conf that you used are wrong, these are for TCP network inputs.
as you can read at https://docs.splunk.com/Documentation/Splunk/9.1.2/Admin/Inputsconf#inputs.conf.example , , the correct ones for forwarding and receiving are
[splunktcp://:9997]
disabled = 0
[splunktcp://:9998]
disabled = 0
[splunktcp://:9999]
disabled = 0Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your response @gcusello
Maybe I do not understand some splunk concepts very well.
All I want is if an event arrives to the port 9998 it should be indexed in the index iscore_test. As if it the event arrives to the port the event should be indexed in the index iscore_prod. The inputs.conf that I setted for this app would be correct?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @aguilard,
as I said which kind of logs are you speaking of?
if syslogs, using the tcp protocol on port 9998 and 9999 the inputs you used are correct, but you cannot see them in the dashboard you shared in the screenshot, you have to search them in the TCP network inputs [Inputs > Network Inputs > TCP].
if instead you want to receive logs from another Splunk system (e.g. a Universal Forwarder) you can see in the dashboard you shared in the screenshot but you have to use the conf files I hinted.
Probably you have some confusion in the kind of inputs: they are two different kind of inputs that are displayed in different dashboards.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
I think I understand now... Yes I want to receive logs from UFW.
In that case I only need to set the inputs.conf file as you said and in the UFWs set the values for index and sourcetype, right?
Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @aguilard,
if you want to receive logs from UFs, you don't need different ports to have different indexes, you can configure the inputs on the Forwarders addressing the correct index, so you can use one input on the indexers that's easier to manage.
The inputs on the Forwarders an be manager by te Deployment Server, for more infos abut this see at https://docs.splunk.com/Documentation/Splunk/9.1.2/Updating/Aboutdeploymentserver
let me know if I can help you more, or, please, accept one answer for the other people of Community.
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The indexes.conf is it copied succesfully and the indexer create the indexes correctly, the problem is the inputs.conf that is not working properly.