Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Getting Data In
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How to search for events with domains on DNS Block...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to search for events with domains on DNS Blocklist?
waJesu
Path Finder
03-17-2023
07:52 AM
I have lookup table with a DNS blocklist. What query can I use to search for events with any of the blocklisted domains. I had received advice to create a csv file with two columns: "Domain" and "suspicious" which is set to 1 for all the domains. Then I would search for the dns sourcetype and suspicious=1. This did not work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tscroggins
Influencer
03-18-2023
08:53 AM
Hi,
Let's assume your events have a field named url_domain. You can combine your lookup with a subsearch to filter events:
index=main [| inputlookup blocklist.csv where suspicious=1 | table Domain | rename Domain as url_domain ]This expands to, for example:
index=main ( ( url_domain="foo.example.com" ) OR ( url_domain="bar.example.com" ) OR ( url_domain="baz.example.com" ) )You can also use lookups for filtering in the search pipeline:
index=main
``` perform pre-filtering tasks here ```
| lookup blocklist.csv Domain as url_domain output suspicious
| search suspicious=1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
waJesu
Path Finder
03-20-2023
04:11 AM
@tscroggins Thank you for the assistance. I tried index=main
| lookup blocklist.csv Domain as url_domain output suspicious
| search suspicious=1
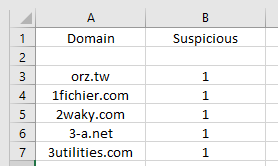
It says "the destination suspicious was not found in the blocklist.csv. My table looks like this:
I am not sure where I missed it.
Get Updates on the Splunk Community!
Get the T-shirt to Prove You Survived Splunk University Bootcamp
As if Splunk University, in Las Vegas, in-person, with three days of bootcamps and labs weren’t enough, now ...
Introducing the Splunk Community Dashboard Challenge!
Welcome to Splunk Community Dashboard Challenge! This is your chance to showcase your skills in creating ...
Wondering How to Build Resiliency in the Cloud?
IT leaders are choosing Splunk Cloud as an ideal cloud transformation platform to drive business resilience, ...