- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- File Comparision
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
File Comparision
I have a file which is being indexed(say today) and then again indexed after updating(say tomorrow). I have to compare the events of the two versions and display the event(s) which is present in the new one but not in old or vice versa. Can any help?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How is the file indexed? How do the events differ from day to day? How many events per file when indexed? What else can you say about the indexing process?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Files are indexed through inputs.cong .
Files differs as.. example file1 indexed today has 1event ZC_01;11;13;30 and when updated and indexed it has 2 events ZC_01;11;13;30
ZC_01;11;13;29
i have to display the result as... ZC_01;11;13;29 this is the newly added data in the updated file1.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do the events from the two different days have different timestamps? Do events from the first indexing also appear in the second indexing (just with different timestamps)?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
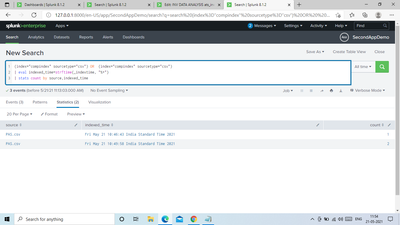
This image can help you understand the scenario.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How about something like this
search 1
| append [search 2]
| eventstats count by _raw
| where count=1- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually sir, i am a very beginner. Can you elaborate the query in an clear way. The above one didn't work. What should i write in place of search 1 and 2?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You might not need two searches if both times the file is indexed they go into the same index
index="compindex"
| eventstats count by _raw
| where count=1The problem with defining your question with non-specific or fabricated examples is that the answers are often just as vague and it takes longer to resolve, but this is the price we pay for anonymisation 😁
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
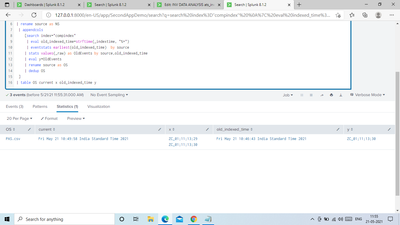
i did this one and got the resutl. thank u sir. and one more help.. how to display it as a table with columns
source time(when file was indexed latest) OnlyThe NewData
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index="compindex"
| eventstats count by _raw
| where count=1
| table source _indextime _raw