- Splunk Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: Textbox input for Dashboard
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Textbox input for Dashboard
Hi All,
@ITWhisperer @renjith_nair @woodcock
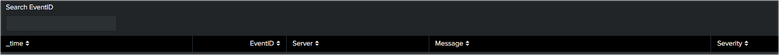
From the above "Textbox" input and panel for (_time, EventID, Server, Message, Severity)
"Textbox" Settings:
<input type="text" token="eventid" searchWhenChanged="true">
<label>Search EventID</label>
</input>
When I search in the "Textbox" using an "EventID", it only displays results based on the EventID values. However, when I search using other parameters such as "_time", "Server", "Message", or "Severity", it does not retrieve any results.
Can anyone assist me with creating a conditional search for any of the following fields in a above table: _time, EventID, Server, Message, or Severity? When I search for any value in these fields, I want the corresponding records to be displayed.
Either in UI or Source need the settings.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| where _time=$eventid$ OR EventID=$eventid$ OR Server=$eventid$ OR Message=$eventid$ OR Severity=$eventid$- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @phanikumarcs,
the input code you share isn't complete, could you share the complete form code?
with special attention to the panel's search that uses the text input token.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gcusello Here is the code
<row>
<panel>
<title>EventID-Severity Matrix</title>
<input type="text" token="eventid" searchWhenChanged="true">
<label>Search EventID</label>
</input>
<table>
<search>
<query>index IN ("foo1", "foo2", "foo3") host IN ("goo1", "goo2", "goo3", "goo4") EventID IN ("1", "1021", "1069") Name=* $eventid$
|fields EventID Name host
| eval Severity=case(
EventID="1", "Information",
EventID="1021", "Warning",
EventID="1069", "Critical",)
| rename Name as Message, host as Server
| table _time, EventID, Server, Message, Severity</query>
<earliest>$time.earliest$</earliest>
<latest>$time.latest$</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @phanikumarcs ,
at first, if you want o use the text input only on eventid input, you should modify your search in :
<row>
<panel>
<title>EventID-Severity Matrix</title>
<input type="text" token="eventid" searchWhenChanged="true">
<label>Search EventID</label>
<prefix>EventID="</prefix>
<suffix>"</suffix>
</input>
<table>
<search>
<query>
index IN ("foo1", "foo2", "foo3") host IN ("goo1", "goo2", "goo3", "goo4") EventID IN ("1", "1021", "1069") Name=* $eventid$
| fields EventID Name host
| eval Severity=case(
EventID="1", "Information",
EventID="1021", "Warning",
EventID="1069", "Critical",)
| rename Name as Message, host as Server
| table _time, EventID, Server, Message, Severity</query>
<earliest>$time.earliest$</earliest>
<latest>$time.latest$</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>otherwise the token will search on the raw text instead on the EventID field.
Then is eventid a field present in all the events or only in part of them?
if you use * in the text box, you exclude from the results the events without the EventID field.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gcusello great, understood.
Suppose when i want to search the Server field value (goo1) in the EventID Textbox, it will display the results of goo1, similar to other fields as well (Message, Severity)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @phanikumarcs ,
you have to declare the field that you want to use for the value in the text input, otherwise it willsearch in the raw text, and e.g. the host field usually isn't in the raw event, but in metadata.
but this add to your dashboard an additional issue: if the eventId field isn't present in all the events, adding event_Id=* will exclude from the results all the events without this field, so beware to how you use this input.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gcusello @ITWhisperer
To clarify, my understanding is that if any fields are included in the '_raw' only will search for those fields, applicable to all input methods (text, dropdown, multi-select, and others). Is that correct?
In this case what is the solution for custom fields like in my query where field ("Severity") values (Critical, Warning, Information).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @phanikumarcs ,
sorry id I'm repeating: if you don't want to search a full text search on _raw, you have to declare the field to associate to each input (every kind of them).
But you have to put attention if some event's don't have one of the fields because the default (e.g. event_id=*) will exclude the events without this field.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At first glance, there doesn't appear to be anything wrong with your search as you have shown it. Please can you give some examples of events which are not found and the search string used which failed to find the events?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, its not about the search
| where _time=$eventid$ OR EventID=$eventid$ OR Server=$eventid$ OR Message=$eventid$ OR Severity=$eventid$
Make it as simple, when you search for specific values in any field (for example, EventID, Server, Message, or Severity) in the search input "Textbox", the system will display relevant data related to those fields. This allows for easy and straightforward searching based on the criteria.
Reference Image:
In the code I provided earlier, what changes are necessary for token-related conditions?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no "search for specific values in any field" - where you have placed the token, it effectively searches the _raw field, and there doesn't appear to be anything wrong here.
You have already got a "token-related condition".
Please provide examples where this is not working for you, particularly with events which should have been found for a particular token value, or events which were found which shouldn't have been.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer
I tried the below search its not working at all.
| where _time=$eventid$ OR EventID=$eventid$ OR Server=$eventid$ OR Message=$eventid$ OR Severity=$eventid$
When i keep this search in the pannel it gives all the desired results.
But, when i search in the "textbox" like values of Severity(Critical or Warning or Information) its not working.
when i search in the "textbox" like values of (EventID or Server or Message) it is working
I think due to Severity is a custom field, so its not working i guess is this right?
the EventID, Name as Message, host as Server fields are from _raw
index=foo host=foo
"$search$" OR Severity="$search$"
| eval Severity=case(EventID="1068", "Warning",
EventID="1", "Information",
EventID="1021", "Warning",
EventID="7011", "Warning",
EventID="6006", "Warning",
EventID="4227", "Warning",
EventID="4231", "Warning",
EventID="1069", "Critical",
EventID="1205", "Critical",
EventID="1254", "Critical",
EventID="1282", "Critical")
| rename Name as Message, host as Server
| table _time EventID Server Message Severity
any suggestions.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When using where and equals, the right hand side is treated as a field name, unless it is numeric, so if you do
| where severity=$eventid$that will translate to
| where severity=informationalwhich will mean it's trying to compare the severity field to the informational field, which is of course not what you want.
You should do this with your where clause
| where strftime(_time, "%F %T")=$eventid|s$ OR EventID=$eventid|s$ OR Server=$eventid|s$ OR Message=$eventid|s$ OR Severity=$eventid|s$The $eventid|s$ will cause the token value to be correctly quoted, so it will become
| where severity="Informational"The reason I have made strftime(_time, "%F %T") is because _time is an epoch, so unless you specify the exact time epoch in seconds it will not match. This allows you to enter an ISO8601 date format YYYY-MM-DD HH:MM:SS
Note that the where clause will not support wildcard. You could change this to a "search" clause rather than a where clause then you could use wildcards in your search text box.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@bowesmana @gcusello @ITWhisperer Thanks for your Ideas for helping me.
finally, I did it with the below addition, it worked what i desired results.
| rename host as Server, Name as Message
| eval Severity=case(
EventID="1068", "Warning",
EventID="1", "Information",
EventID="1021", "Warning",
EventID="7011", "Warning",
EventID="6006", "Warning",
EventID="4227", "Warning",
EventID="4231", "Warning",
EventID="1069", "Critical",
EventID="1205", "Critical",
EventID="1254", "Critical",
EventID="1282", "Critical")
| fields Server, EventID, Message, Severity
| search Severity="*$search$*" OR EventID="*$search$*" OR Server="*$search$*" OR Message="*$search$*"
| table _time, Server, EventID, Message, Severity- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @phanikumarcs ,
good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated by all the contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@bowesmana unfortunately its not working, the only issue i guess is the custom filed "Severity" creating issue here.
i tried a lot of different searches but no use.